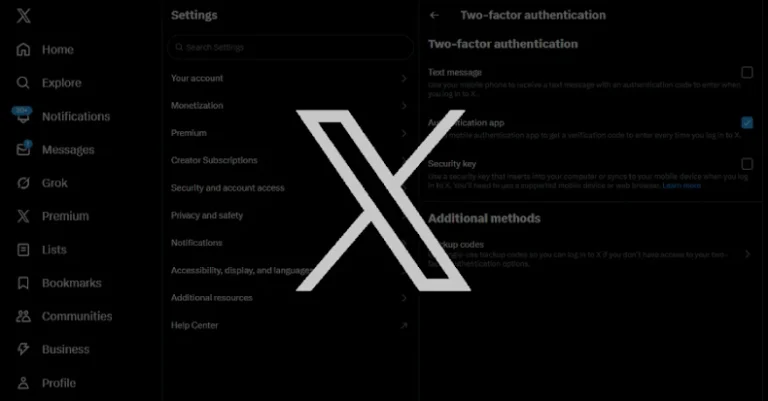
X Warns Users With Security Keys to Re-Enroll Before November 10 to Avoid Lockouts
Social media platform X is urging users who have enrolled for two-factor authentication (2FA) using passkeys and hardware security keys like Yubikeys to re-enroll their key to ensure continued access to the service. To that end, users are being asked to complete the re-enrollment, either using their existing security key or enrolling a new one,…