67% of ChatGPT’s Top 1,000 Citations Are Off-Limits to Marketers (+ More Findings)
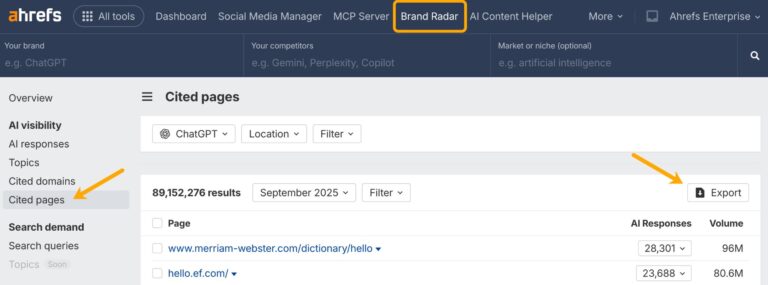
I analyzed the top 1,000 pages ChatGPT cited in September 2025 using Ahrefs Brand Radar, to understand what types of content AI is referencing right now. You can repeat this analysis yourself pretty easily. Just do an open database search in Brand Radar, head to the “Cited pages” report for your desired AI assistant, and export…