New FileFix Variant Delivers StealC Malware Through Multilingual Phishing Site
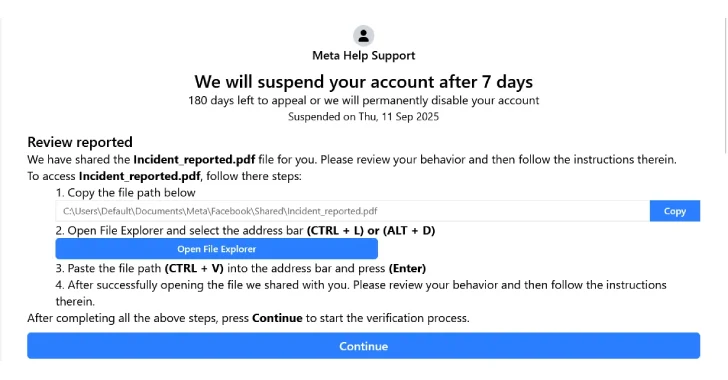
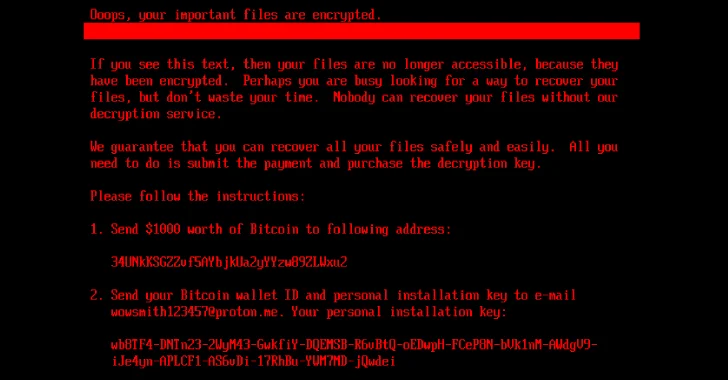
Cybersecurity researchers have warned of a new campaign that’s leveraging a variant of the FileFix social engineering tactic to deliver the StealC information stealer malware. “The observed campaign uses a highly convincing, multilingual phishing site (e.g., fake Facebook Security page), with anti-analysis techniques and advanced obfuscation to evade detection,” Acronis security researcher Eliad Kimhy said…