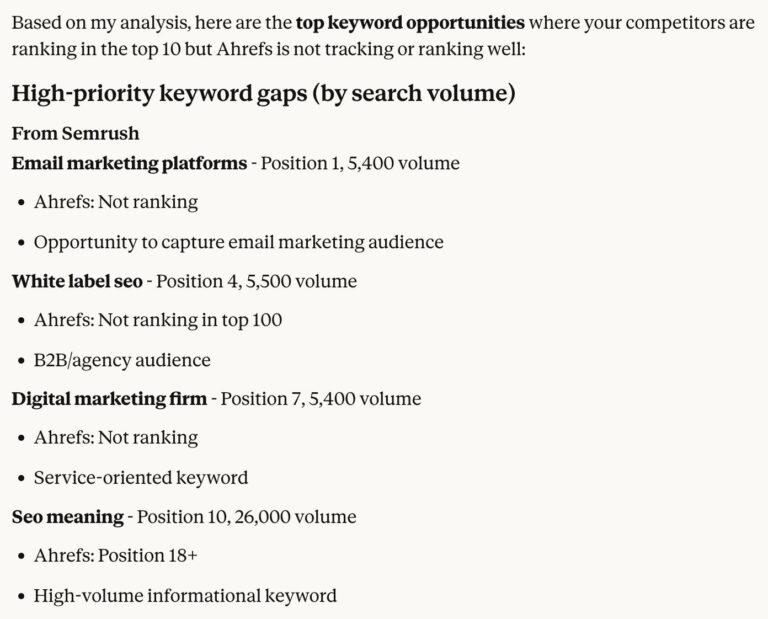
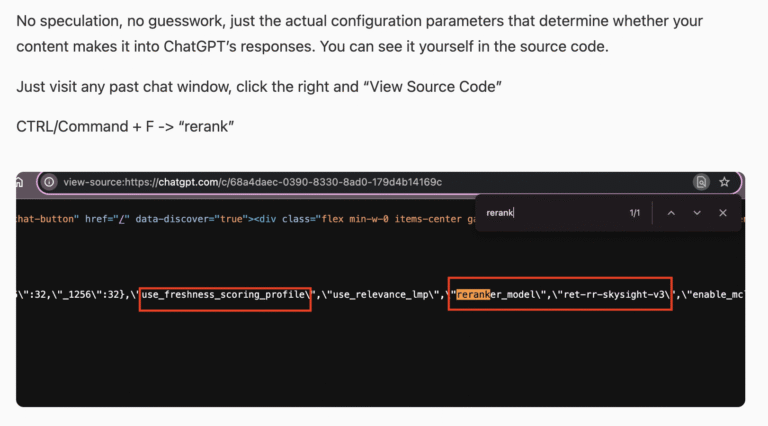
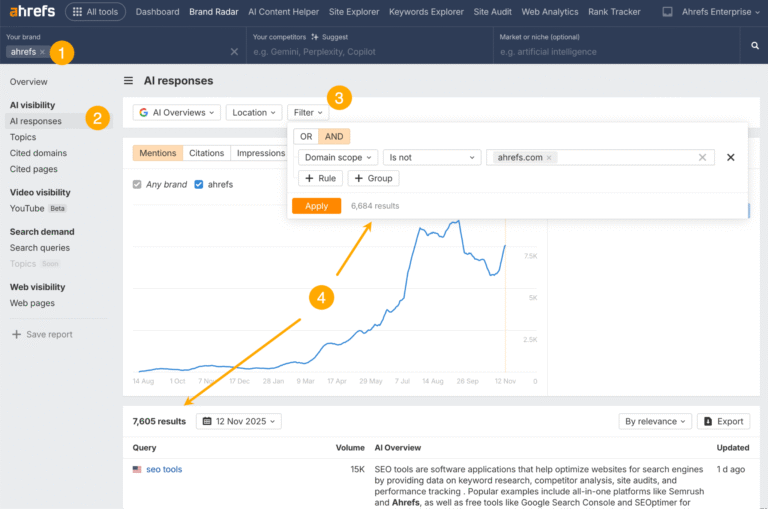
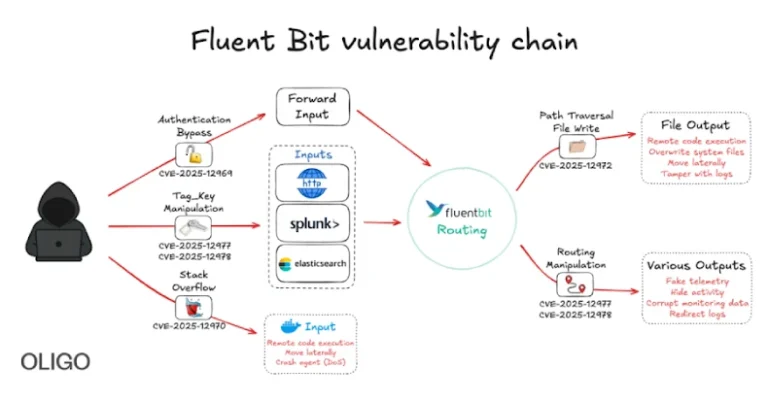
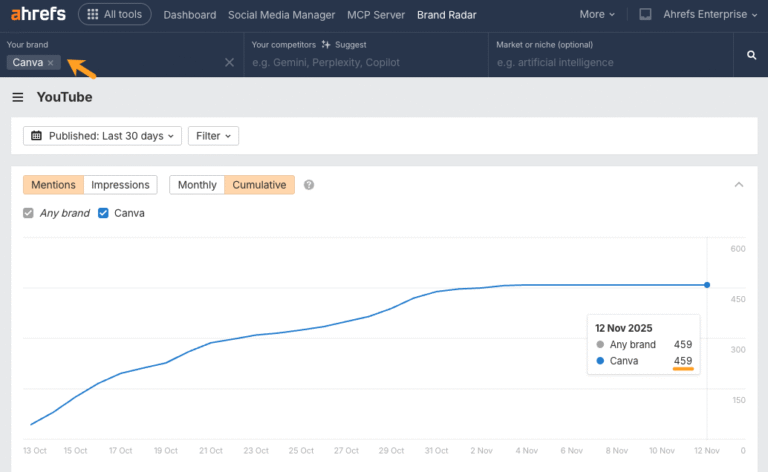
What Is an MCP Server, and Why Should Marketers Care?
MCP (Model Context Protocol) connects your AI tools directly to your marketing stack—your CMS, analytics, CRM, social platforms, and more—through one standardized connection. This means you can ask: ‘Show me which blog posts lost traffic last month, what keywords they rank for in Ahrefs, and how many support tickets mentioned those topics in Intercom’—and get…