JPCERT Confirms Active Command Injection Attacks on Array AG Gateways
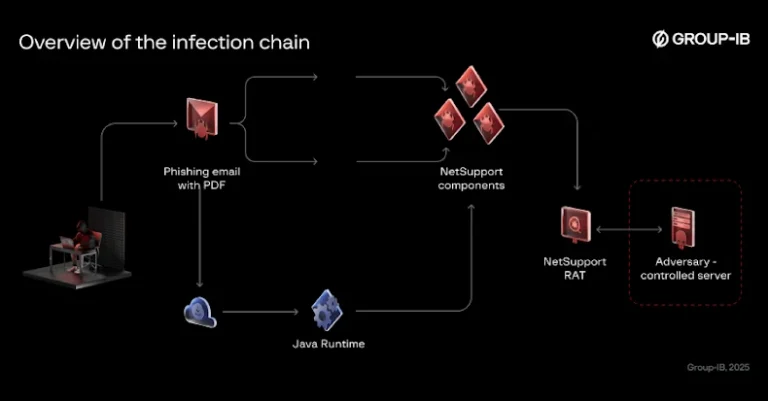
A command injection vulnerability in Array Networks AG Series secure access gateways has been exploited in the wild since August 2025, according to an alert issued by JPCERT/CC this week. The vulnerability, which does not have a CVE identifier, was addressed by the company on May 11, 2025. It’s rooted in Array’s DesktopDirect, a remote…