Cybersecurity researchers have found that bad actors are continuing to have success by spoofing sender email addresses as part of various malspam campaigns.
Faking the sender address of an email is widely seen as an attempt to make the digital missive more legitimate and get past security mechanisms that could otherwise flag it as malicious.
While there are safeguards such as DomainKeys Identified Mail (DKIM), Domain-based Message Authentication, Reporting and Conformance (DMARC), and Sender Policy Framework (SPF) that can be used to prevent spammers from spoofing well-known domains, it has increasingly led them to leverage old, neglected domains in their operations.
In doing so, the email messages are likely to bypass security checks that rely on the domain age as a means to identify spam.
DNS threat intelligence firm, in a new analysis shared with The Hacker News, discovered that threat actors, including Muddling Meerkat and others, have abused some of its own old, disused top-level domains (TLDs) that haven’t been used to host content for nearly 20 years.
“They lack most DNS records, including those that are typically used to check the authenticity of a sender domain, e.g., Sender Policy Framework (SPF) records,” the company said. “The domains are short and in highly reputable TLDs.”

One such campaign, active since at least December 2022, involves distributing email messages with attachments containing QR codes that lead to phishing sites. It also instructs recipients to open the attachment and use the AliPay or WeChat apps on their phones to scan the QR code.
The emails employ tax-related lures written in Mandarin, while also locking the QR code documents behind a four-digit password included in the email body in different ways. The phishing site, in one case, urged users to enter their identification and card details, and then make a fraudulent payment to the attacker.
“Although the campaigns do use the neglected domains we see with Muddling Meerkat, they appear to broadly spoof random domains, even ones that do not exist,” Infoblox explained. “The actor may use this technique to avoid repeated emails from the same sender.”
The company said it also observed phishing campaigns that impersonate popular brands like Amazon, Mastercard, and SMBC to redirect victims to fake login pages using traffic distribution systems (TDSes) with an aim to steal their credentials. Some of the email addresses that have been identified as using spoofed sender domains are listed below –
- ak@fdd.xpv[.]org
- mh@thq.cyxfyxrv[.]com
- mfhez@shp.bzmb[.]com
- gcini@vjw.mosf[.]com
- iipnf@gvy.zxdvrdbtb[.]com
- zmrbcj@bce.xnity[.]net
- nxohlq@vzy.dpyj[.]com
A third category of spam relates to extortion, wherein email recipients are asked to make a $1800 payment in Bitcoin to delete embarrassing videos of themselves that were recorded using a purported remote access trojan installed on their systems.
“The actor spoofs the user’s own email address and challenges them to check it and see,” Infoblox The email tells the user that their device has been compromised, and as proof, the actor alleges that the message was sent from the user’s own account.”
The disclosure comes as legal, government and construction sectors have been targeted by a new phishing campaign dubbed Butcher Shop that aims to steal Microsoft 365 credentials since early September 2024.
- How to build a website with WordPress and what are the best plugins to use: WordPress Web Design Tutorials: How to build a website with WordPress and what are the best plugins to use. Building a website with WordPress is an excellent choice due to its versatility, ease of use, and a vast array of plugins that enhance functionality. Here’s a comprehensive guide to building a WordPress website, along with recommendations for the best plugins.
- The Most Important Stages and Plugins for WordPress Website Development: Developing a WordPress website requires careful planning, execution, and optimisation to ensure it is functional, user-friendly, and effective. The process can be broken into key stages, and each stage benefits from specific plugins to enhance functionality and performance. Here’s a detailed guide to the most important stages of WordPress website development and the essential plugins for each stage.
- What are the most powerful Tools for SEO in WordPress?: Powerful SEO Tools for WordPress: Search Engine Optimisation (SEO) is essential for improving your WordPress website’s visibility in search engines. Here are the most powerful tools to optimise your site effectively:
- How to add shipping modules in CubeCart: Step 1: Log in to Your CubeCart Admin Panel: Open your web browser and navigate to your CubeCart admin login page. Enter your username and password to log in.
Step 2: Navigate to the Extensions Section: Once logged in, go to the left-hand menu and click on Manage Extensions. From the dropdown, select Extensions.
Step 3: Find Shipping Modules: In the Extensions section, locate the Shipping tab to view available shipping modules. You can browse through the list or use the search function to find a specific module. - Gathering domain and IP information with Whois and Dig: In the digital age, understanding the intricacies of domain and IP information is essential for anyone navigating the online landscape. This article explores two powerful tools—WHOIS and DIG—that help gather valuable insights about websites and their underlying infrastructure. Whether you’re a cybersecurity professional, a web developer, or simply curious about online resources, you will learn how to effectively utilize these tools, interpret their outputs, and apply this knowledge to real-world scenarios.
- What are the best WordPress Security plugins and how to set them up the best way: Read a comprehensive guide on the best WordPress security plugins and how to set them up to ensure optimal protection for your WordPress site.
- Will a headland provide enough shelter?
- Learn How To Purchase Your Own Domain Name with Fastdot.com: Open your web browser and go to Fastdot.com. Navigate to the Domains section, either from the homepage or from the main navigation bar.
Step 2: Search for Your Desired Domain Name: In the domain search bar, type the domain name you want to purchase. Fastdot supports a wide range of domain extensions (TLDs), such as .com, .net, .org, .com.au, and many others. Click the Search Domain button. The system will check the availability of your desired domain name.
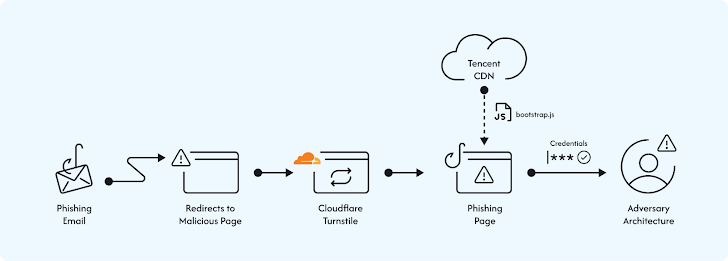
The attacks, per Obsidian Security, abuse trusted platforms like Canva, Dropbox DocSend, and Google Accelerated Mobile Pages (AMPs) to redirect users to the malicious sites. Some of the other channels include emails and compromised WordPress sites.
“Before displaying the phishing page, a custom page with a Cloudflare Turnstile is shown to verify that the user is, in fact, human,” the company said. “These turnstiles make it harder for email protection systems, like URL scanners, to detect phishing sites.”
In recent months, SMS phishing campaigns have been observed impersonating law enforcement authorities in the U.A.E. to send fake payment requests for non-existent traffic violations, parking violations, and license renewals. Some of the bogus sites set up for this purpose have been attributed to a known threat actor called Smishing Triad.
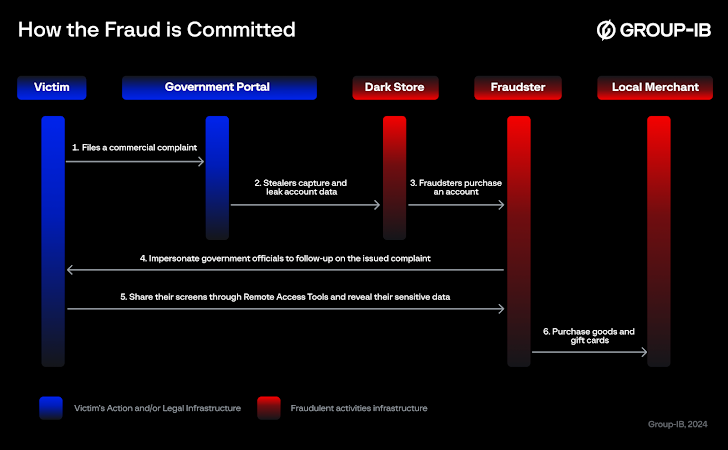
Banking customers in the Middle East have also been targeted by a sophisticated social engineering scheme that impersonates government officials in phone calls and employs remote access software to steal credit card information and one-time passwords (OTPs).
The campaign, assessed to be the work of unknown native Arabic speakers, has been found to be primarily directed against female consumers who have had their personal data leaked via stealer malware on the dark web.
“The scam specifically targets individuals who have previously submitted commercial complaints to the government services portal, either through its website or mobile app, regarding products or services purchased from online merchants,” Group-IB said in an analysis published today.

“The fraudsters exploit the victims’ willingness to cooperate and obey their instructions, hoping to receive refunds for their unsatisfactory purchases.”
Another campaign identified by Cofense involves sending emails claiming to be from the United States Social Security Administration that embed a link to download an installer for the ConnectWise remote access software or direct the victims to credential harvesting pages.
The development comes as generic top-level domains (gTLDs) such as .top, .xyz, .shop, .vip, and .club have accounted for 37% of cybercrime domains reported between September 2023 and August 2024, despite holding only 11% of the total domain name market, according to a report from the Interisle Consulting Group.
These domains have become lucrative for malicious actors due to low prices and a lack of registration requirements, thereby opening doors for abuse. Among the gTLDs widely used for cybercrime, 22 offered registration fees of less than $2.00.
Threat actors have also been discovered advertising a malicious WordPress plugin called PhishWP that can be used to create customizable payment pages mimicking legitimate payment processors like Stripe to steal personal and financial data via Telegram.
“Attackers can either compromise legitimate WordPress websites or set up fraudulent ones to install it,” SlashNext said in a new report. “After configuring the plugin to mimic a payment gateway, unsuspecting users are lured into entering their payment details. The plugin collects this information and sends it directly to attackers, often in real-time.”